内存取证挑战,Lab1~6
Lab 1 Beginner’s Luck
Easy1
2volatility -f MemoryDump_Lab1.raw imageinfo # 检测profile类型
volatility -f MemoryDump_Lab1.raw --profile=Win7SP1x64 consoles # 获取cmd的指令和结果(cmdscan只包括cmd指令)
得到cmd的缓存中有St4G3$1的运行结果ZmxhZ3t0aDFzXzFzX3RoM18xc3Rfc3Q0ZzMhIX0解码得到flag{th1s_1s_th3_1st_st4g3!!}。
内存数据通过DumpIt.exe获取。
Lab 2 A New World
Easy1
volatility -f MemoryDump_Lab2.raw --profile=Win7SP1x64 envars # 查看环境变量
存在NEW_TMP环境变量,值为C:\Windows\ZmxhZ3t3M2xjMG0zX1QwXyRUNGczXyFfT2ZfTDRCXzJ9,解码得到flag{w3lc0m3_T0_$T4g3_!_Of_L4B_2}。
Lab 3 The Evil’s Den
InCTF 2018 Evil Crypter
Easy - Medium1
2
3
4volatility -f MemoryDump_Lab3.raw imageinfo # Win7SP1x86
volatility -f MemoryDump_Lab3.raw --profile=Win7SP1x86 iehistory # ie浏览器历史,在Desktop目录下有可疑文件suspision1.jpeg、evilscript.py.py和vip.txt
volatility -f MemoryDump_Lab3.raw --profile=Win7SP1x86 filescan # 扫描文件,获取文件对应的Offset
volatility -f MemoryDump_Lab3.raw --profile=Win7SP1x86 dumpfiles -D ./files -Q 0x000000003e727e50 -n # 提取vip.txt,其余文件同理
第一部分根据evilscript.py.py(先xor(3)后base64)和加密结果vip.txt可以逆向得到inctf{0n3_h4lf;根据提示使用steghide extract -sf suspision1.jpeg提取suspision1.jpeg中的隐藏信息,密码为inctf{0n3_h4lf,得到第二部分_1s_n0t_3n0ugh},即为inctf{0n3_h4lf_1s_n0t_3n0ugh}。
Lab 4 Obsession
Just Do It - InCTF Internationals 2019
Medium1
2
3volatility -f MemoryDump_Lab4.raw imageinfo # Win7SP1x64
volatility -f MemoryDump_Lab4.raw --profile=Win7SP1x64 iehistory # 发现Important.txt但无法dumpfiles
volatility -f MemoryDump_Lab4.raw --profile=Win7SP1x64 mftparser > mftparse # 利用MFT查看Important.txtImportant.txt已被删除,无法通过dumpfiles获取。使用mftparser检查NTFS的主控文件表MFT的$DATA属性(每个MFT表项为1024字节),参考OMFW 2012: Reconstructing the MBR and MFT from Memory。最后在mftparse中得到inctf{1_is_n0t_EQu4l_7o_2_bUt_th1s_d0s3nt_m4ke_s3ns3}。
Lab 5 Black Tuesday
Medium - Hard1
2
3
4volatility -f MemoryDump_Lab5.raw imageinfo # Win7SP1x64
volatility -f MemoryDump_Lab5.raw --profile=Win7SP1x64 iehistory
volatility -f MemoryDump_Lab5.raw --profile=Win7SP1x64 filescan # SW1wb3J0YW50.rar
volatility -f MemoryDump_Lab5.raw --profile=Win7SP1x64 dumpfiles -D ./files -Q 0x000000003eed56f0 -n
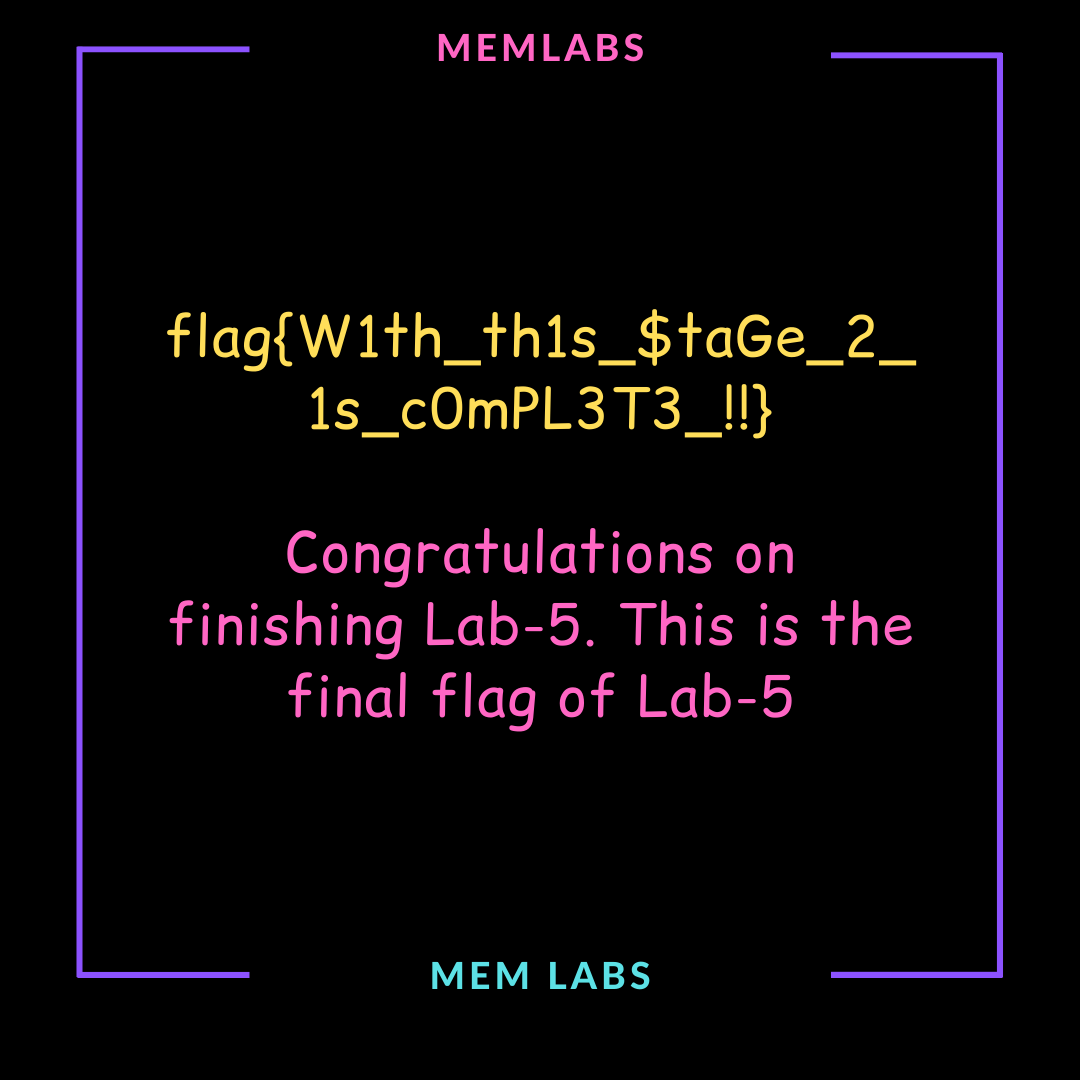
在iehistory中找到记录C:/Windows/AppPatch/ZmxhZ3shIV93M0xMX2QwbjNfU3Q0ZzMtMV8wZl9MNEJfNV9EMG4zXyEhfQ.bmp,base64解密得到flag{!!_w3LL_d0n3_St4g3-1_0f_L4B_5_D0n3_!!}。在filescan中找到记录\Device\HarddiskVolume2\Users\SmartNet\Documents\SW1wb3J0YW50.rar,dumpfiles下来后使用上一flag作为密码解压,得到Stage2.png,得到第二个flag,为flag{W1th_th1s_$taGe_2_1s_c0mPL3T3_!!}。
Lab 6 The Reckoning
Hard1
2
3
4
5volatility -f MemoryDump_Lab6.raw imageinfo # Win7SP1x64
volatility -f MemoryDump_Lab6.raw --profile=Win7SP1x64 iehistory
volatility -f MemoryDump_Lab6.raw --profile=Win7SP1x64 filescan # flag.rar History
volatility -f MemoryDump_Lab6.raw --profile=Win7SP1x64 pstree # WinRAR.exe 3716
volatility -f MemoryDump_Lab6.raw --profile=Win7SP1x64 envars -p 3716 # RAR password easypeasyvirus
查看WinRAR.exe的环境变量发现密码,解密flag.rar得到flag2.png,为aN_Am4zING_!_i_gU3Ss???_}。

1 | volatility -f MemoryDump_Lab6.raw --profile=Win7SP1x64 dumpfiles -D ./files -Q 0x000000005da5a610 -n # History.vacb History.dat |
检查Chrome的\User Data\Default\History,获得sqlite3数据库文件History.dat,查找记录sqlite3 History.dat "select url from urls;"发现可疑网址https://pastebin.com/RSGSi1hk。
里面有一Google文档的地址,打开后为一大段拉丁语文字,中间有一个MEGA链接,但是存在密码保护。搜索整个内存cat MemoryDump_Lab6.raw.strings | grep -i mega | grep -i key,发现THE KEY IS zyWxCjCYYSEMA-hZe552qWVXiPwa5TecODbjnsscMIU即为下载密钥,获得flag_.png,为另一半flag:inctf{thi5_cH4LL3Ng3_!s_g0nn4_b3_?_。
(也可以通过screenshot获取浏览器标题然后再搜索)

inctf{thi5_cH4LL3Ng3_!s_g0nn4_b3_?_aN_Am4zINg_!_i_gU3Ss???_}