Briefings 在 8.7~8.8 举行,共 21 类,123 个议题

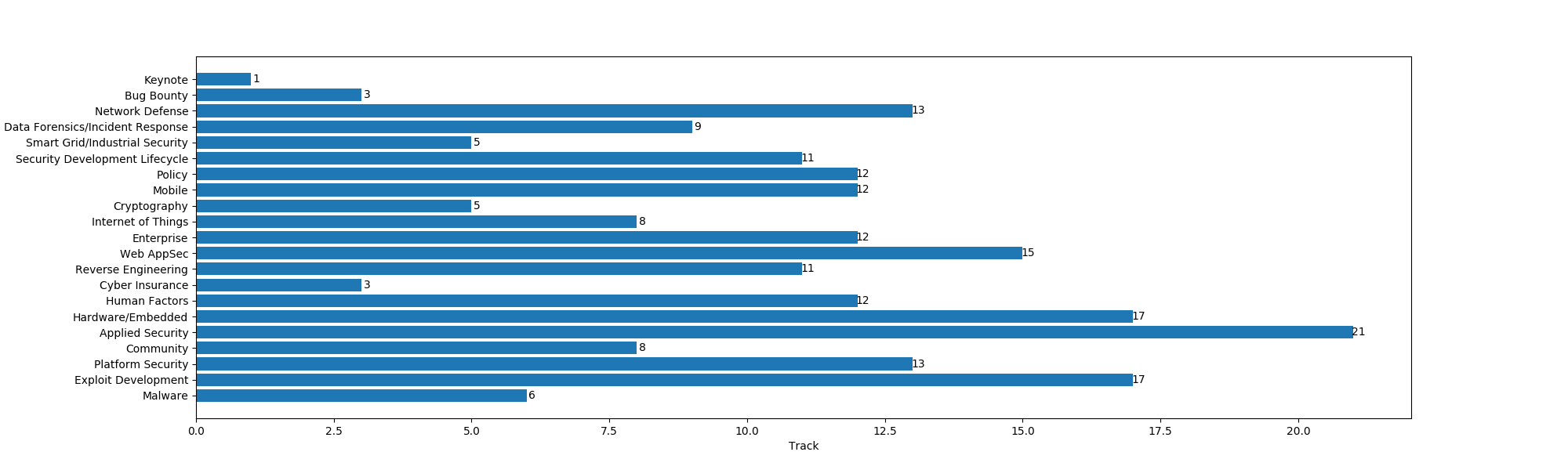
TRACKS
- Malware 6
- Exploit Development 17
- Platform Security 13
- Community 8
- Applied Security 21
- Hardware/Embedded 17
- Human Factors 12
- Cyber Insurance 3
- Reverse Engineering 11
- Web AppSec 15
- Enterprise 12
- Internet of Things 8
- Cryptography 5
- Mobile 12
- Policy 12
- Security Development Lifecycle 11
- Smart Grid/Industrial Security 5
- Data Forensics/Incident Response 9
- Network Defense 13
- Bug Bounty 3
- Keynote 1
TITLES
| Titles | Speakers | Tracks | |
|---|---|---|---|
| 1 | Flying a False Flag: Advanced C2, Trust Conflicts, and Domain Takeover GitHub | Nick Landers | Malware |
| 2 | Battle of Windows Service: A Silver Bullet to Discover File Privilege Escalation Bugs Automatically | Wenxu Wu | Exploit Development,Platform Security |
| 3 | Hacking Your Non-Compete | Brian Dykstra,Gregory Stone | Community |
| 4 | He Said, She Said – Poisoned RDP Offense and Defense | Eyal Itkin,Dana Baril | Exploit Development,Applied Security |
| 5 | Lessons and Lulz: The 5th Annual Black Hat USA NOC Report | Bart Stump,Neil Wyler | Applied Security |
| 6 | Biometric Authentication Under Threat: Liveness Detection Hacking | Zhuo Ma,Bin Ma,Yu Chen | Hardware/Embedded,Human Factors |
| 7 | How Do Cyber Insurers View The World? | Matt Prevost | Cyber Insurance |
| 8 | Hunting for Bugs, Catching Dragons 对 Outlook/Exchange 漏洞及利用的总结 | Nicolas Joly | Reverse Engineering,Exploit Development |
| 9 | Internet-Scale Analysis of AWS Cognito Security | Andres Riancho | Web AppSec,Enterprise |
| 10 | Moving from Hacking IoT Gadgets to Breaking into One of Europe’s Highest Hotel Suites | Michael Huebler,Ray . | Hardware/Embedded,Internet of Things |
| 11 | Messaging Layer Security: Towards a New Era of Secure Group Messaging | Katriel Cohn-Gordon,Raphael Robert,Benjamin Beurdouche | Applied Security,Cryptography |
| 12 | Bypassing the Maginot Line: Remotely Exploit the Hardware Decoder on Smartphone | Peter Pi,Xiling Gong | Exploit Development,Mobile |
| 13 | The Cyber Shell Game – War, Information Warfare, and the Darkening Web | Alexander Klimburg | Policy |
| 14 | Cybersecurity Risk Assessment for Safety-Critical Systems | Daniel Johnson,Ken Heffner,Ly Vessels | Security Development Lifecycle,Smart Grid/Industrial Security |
| 15 | ClickOnce and You’re in - When Appref-ms Abuse is Operating as Intended | William Burke | Human Factors,Applied Security |
| 16 | Deconstructing the Phishing Campaigns that Target Gmail Users | Daniela Oliveira,Elie Bursztein | Human Factors |
| 17 | Detecting Deep Fakes with Mice | Alex Comerford,Jonathan Saunders,George Williams | Human Factors,Data Forensics/Incident Response |
| 18 | Defense Against Rapidly Morphing DDOS | Mikhail Fedorov,Mudit Tyagi | Enterprise,Network Defense |
| 19 | Detecting Malicious Files with YARA Rules as They Traverse the Network | David Bernal | Data Forensics/Incident Response,Network Defense |
| 20 | Going Beyond Coverage-Guided Fuzzing with Structured Fuzzing | Jonathan Metzman | Security Development Lifecycle |
| 21 | Paging All Windows Geeks – Finding Evil in Windows 10 Compressed Memory | Dimiter Andonov,Omar Sardar | Reverse Engineering,Data Forensics/Incident Response |
| 22 | MINimum Failure - Stealing Bitcoins with Electromagnetic Fault Injection | Colin O’Flynn | Mobile,Hardware/Embedded |
| 23 | PeriScope: An Effective Probing and Fuzzing Framework for the Hardware-OS Boundary | Dokyung Song | Platform Security,Mobile |
| 24 | Reverse Engineering WhatsApp Encryption for Chat Manipulation and More | Oded Vanunu,Roman Zaikin | Reverse Engineering,Web AppSec |
| 25 | Legal GNSS Spoofing and its Effects on Autonomous Vehicles | Victor Murray | Hardware/Embedded,Internet of Things |
| 26 | Transparency in the Software Supply Chain: Making SBOM a Reality | Allan Friedman | Security Development Lifecycle,Policy |
| 27 | Monsters in the Middleboxes: Building Tools for Detecting HTTPS Interception | Gabriele Fisher,Luke Valenta | Web AppSec,Network Defense |
| 28 | Attack Surface as a Service | Anna Westelius | Web AppSec |
| 29 | Death to the IOC: What’s Next in Threat Intelligence | Bhavna Soman | Enterprise,Data Forensics/Incident Response |
| 30 | GDPArrrrr: Using Privacy Laws to Steal Identities | James Pavur | Human Factors,Policy |
| 31 | SSO Wars: The Token Menace | Oleksandr Mirosh,Alvaro Munoz | Enterprise,Web AppSec |
| 32 | Mobile Interconnect Threats: How Next-Gen Products May be Already Outdated | Guillaume Teissier | Exploit Development,Network Defense |
| 33 | On Trust: Stories from the Front Lines | Jamil Farshchi | Enterprise |
| 34 | Shifting Knowledge Left: Keeping up with Modern Application Security | Fletcher Heisler,Mark Stanislav | Human Factors,Security Development Lifecycle |
| 35 | APIC’s Adventures in Wonderland | Frank Block,Oliver Matula | Exploit Development,Network Defense |
| 36 | Testing Your Organization’s Social Media Awareness | Jacob Wilkin | Human Factors |
| 37 | The Future of Securing Intelligent Electronic Devices Using the IEC 62351-7 Standard for Monitoring | Younes Dragoni,Alessandro Di Pinto,Andrea Carcano | Smart Grid/Industrial Security |
| 38 | Attacking and Defending the Microsoft Cloud (Office 365 & Azure AD) | Mark Morowczynski,Sean Metcalf | Network Defense,Enterprise |
| 39 | WebAuthn 101 - Demystifying WebAuthn | Christiaan Brand | Web AppSec,Applied Security |
| 40 | Woke Hiring Won’t Save Us: An Actionable Approach to Diversity Hiring and Retention | Rebecca Lynch | Policy,Community |
| 41 | 100 Seconds of Solitude: Defeating Cisco Trust Anchor With FPGA Bitstream Shenanigans | Ang Cui,Richard Housley,Jatin Kataria | Reverse Engineering,Hardware/Embedded |
| 42 | Attacking Electric Motors for Fun and Profit | Duminda Wijesekera,Matthew Jablonski | Internet of Things,Smart Grid/Industrial Security |
| 43 | All Your Apple are Belong to Us: Unique Identification and Cross-Device Tracking of Apple Devices | Xiaolong Bai,Min Zheng | Applied Security,Mobile |
| 44 | Behind the Scenes: The Industry of Social Media Manipulation Driven by Malware | Olivier Bilodeau,Masarah Paquet-Clouston | Malware,Human Factors |
| 45 | Breaking Through Another Side: Bypassing Firmware Security Boundaries from Embedded Controller | Alexandre Gazet,Alex Matrosov | Platform Security,Reverse Engineering |
| 46 | Denial of Service with a Fistful of Packets: Exploiting Algorithmic Complexity Vulnerabilities | David Renardy,Nathan Hauke | Exploit Development,Web AppSec |
| 47 | Information Security in the Public Interest | Bruce Schneier | Policy,Community |
| 48 | Planning a Bug Bounty: The Nuts and Bolts from Concept to Launch | Adam Ruddermann | Bug Bounty |
| 49 | Dragonblood: Attacking the Dragonfly Handshake of WPA3 | Mathy Vanhoef | Network Defense,Cryptography |
| 50 | Exploiting the Hyper-V IDE Emulator to Escape the Virtual Machine | Joe Bialek | Platform Security,Exploit Development |
| 51 | Playing Offense and Defense with Deepfakes | Matt Price,Mike Price | Human Factors |
| 52 | Project Zero: Five Years of ‘Make 0Day Hard’ | Ben Hawkes | Platform Security,Exploit Development |
| 53 | Hacking for the Greater Good: Empowering Technologists to Strengthen Digital Society | Eva Galperin,Camille Francois,Bruce Schneier | Community |
| 54 | Rough and Ready: Frameworks to Measure Persistent Engagement and Deterrence | Neil Jenkins,Jason Healey | Data Forensics/Incident Response,Policy |
| 55 | The Enemy Within: Modern Supply Chain Attacks | Eric Doerr | Data Forensics/Incident Response,Enterprise |
| 56 | PicoDMA: DMA Attacks at Your Fingertips | Ben Blaxill,Joel Sandin | Platform Security,Hardware/Embedded |
| 57 | API-Induced SSRF: How Apple Pay Scattered Vulnerabilities Across the Web | Joshua Maddux | Applied Security,Web AppSec |
| 58 | Bounty Operations: Best Practices and Common Pitfalls to Avoid in the First 6-12 Months | Josh Jay,Greg Caswell,Shannon Sabens,Jarek Stanley | Bug Bounty |
| 59 | The Most Secure Browser? Pwning Chrome from 2016 to 2019 | Gengming Liu,Zhen Feng | Exploit Development,Platform Security |
| 60 | Breaking Encrypted Databases: Generic Attacks on Range Queries | Marie-Sarah Lacharite | Cryptography |
| 61 | DevSecOps : What, Why and How | Anant Shrivastava | Security Development Lifecycle,Applied Security |
| 62 | Finding Our Path: How We’re Trying to Improve Active Directory Security介绍 BloodHound,BloodHound 将获取 Domain Admin 方式以地图方式展示出来,并且能计算出最佳路径,大大提高了域渗透的效率 | Will Schroeder,Rohan Vazarkar,Andy Robbins | Enterprise |
| 63 | All the 4G Modules Could be Hacked百度安全实验室,移动网络 4G 安全攻击面 | Zhang Ye,Zheng Huang,Haikuo Xie,Shupeng Gao | Hardware/Embedded,Internet of Things |
| 64 | Operational Templates for State-Level Attack and Collective Defense of Countries | Robert Fanelli,Gregory Conti | Applied Security,Network Defense |
| 65 | Process Injection Techniques - Gotta Catch Them AllWindows 10 x64 进程注入技术总结(有开源代码),CFG 和 CIG 对各种技术的影响 | Amit Klein,Itzik Kotler | Exploit Development,Malware |
| 66 | Rogue7: Rogue Engineering-Station Attacks on S7 Simatic PLCs | Eli Biham,Avishai Wool,Sara Bitan,Uriel Malin | Reverse Engineering,Smart Grid/Industrial Security |
| 67 | Behind the Scenes of Intel Security and Manageability Engine | Yanai Moyal,Shai Hasarfaty | Applied Security,Hardware/Embedded |
| 68 | Women in Security: Building a Female InfoSec Community in Korea, Japan, and Taiwan | Hazel Yen,Suhee Kang,Asuka Nakajima | Community |
| 69 | Cyber Insurance 101 for CISO’s | Jeffrey Smith | Cyber Insurance |
| 70 | 0-days & Mitigations: Roadways to Exploit and Secure Connected BMW Cars | Hendrik Schweppe,Michael Gruffke,Wenkai Zhang,Aohui Wang,Zhiqiang Cai | Hardware/Embedded,Internet of Things |
| 71 | Behind the scenes of iOS and Mac Security | Ivan Krstić | Mobile,Platform Security |
| 72 | HTTP Desync Attacks: Smashing into the Cell Next Door | James Kettle | Web AppSec |
| 73 | Exploiting Qualcomm WLAN and Modem Over The Air腾讯安全 Blade Team,利用 WiFi 漏洞 RCE | Peter Pi,Xiling Gong | Exploit Development,Mobile |
| 74 | Firmware Cartography: Charting the Course for Modern Server Compromise | Dionysus Blazakis,Nathan Keltner | Platform Security,Hardware/Embedded |
| 75 | Ghidra - Journey from Classified NSA Tool to Open Source | Chris Delikat,Brian Knighton | Reverse Engineering |
| 76 | I’m Unique, Just Like You: Human Side-Channels and Their Implications for Security and Privacy | Matt Wixey | Applied Security,Human Factors |
| 77 | Infighting Among Russian Security Services in the Cyber Sphere | Kimberly Zenz | Policy |
| 78 | It’s Not What You Know, It’s What You Do: How Data Can Shape Security Engagement | Aika Sengirbay,Masha Sedova | Human Factors |
| 79 | Managing for Success: Maintaining a Healthy Bug Bounty Program Long Term | Chloe Brown | Bug Bounty |
| 80 | Practical Approach to Automate the Discovery and Eradication of Open-Source Software Vulnerabilities at Scale | Aladdin Almubayed | Web AppSec,Security Development Lifecycle |
| 81 | New Vulnerabilities in 5G Networks5G 商用网络的漏洞,漏洞可被利用实现中间人劫持和定向攻击 | Ravishankar Borgaonkar,Altaf Shaik | Network Defense,Mobile |
| 82 | Predictive Vulnerability Scoring System | Jay Jacobs,Michael Roytman | Network Defense,Enterprise |
| 83 | Selling 0-Days to Governments and Offensive Security Companies对 0-Day 市场买卖交易双方的介绍(和 ISC2019 的相同) | Maor Shwartz,Maor Shwartz | Policy,Community,Policy,Community |
| 84 | Zombie Ant Farming: Practical Tips for Playing Hide and Seek with Linux EDRs | Dimitry Snezhkov | Applied Security,Malware |
| 85 | Automation Techniques in C++ Reverse Engineering | Rolf Rolles | Reverse Engineering |
| 86 | Backdooring Hardware Devices by Injecting Malicious Payloads on Microcontrollers | Sheila Ayelen Berta | Reverse Engineering,Hardware/Embedded |
| 87 | Sensor and Process Fingerprinting in Industrial Control Systems | Mujeeb Ahmed Chuadhry,Martin Ochoa | Applied Security,Smart Grid/Industrial Security |
| 88 | Critical Zero Days Remotely Compromise the Most Popular Real-Time OS | Dor Zusman,Ben Seri | Network Defense,Internet of Things |
| 89 | Fantastic Red-Team Attacks and How to Find Them | Ross Wolf,Casey Smith | Applied Security,Data Forensics/Incident Response |
| 90 | The Path Less Traveled: Abusing Kubernetes Defaults | Duffie Cooley,Ian Coldwater | Platform Security |
| 91 | Inside the Apple T2 | Jeremy Erickson,Mikhail Davidov | Hardware/Embedded,Platform Security |
| 92 | Chip.Fail - Glitching the Silicon of the Connected World | Josh Datko,Thomas Roth | Internet of Things,Hardware/Embedded |
| 93 | Making Big Things Better the Dead Cow Way | Luke Benfey,Christien Rioux,Peiter Mudge Zatko,Joseph Menn | Community |
| 94 | Come Join the CAFSA - Continuous Automated Firmware Security Analysis固件分析工具 FwAnalyzer 的详细介绍,针对文件系统的静态分析,并不针对漏洞发现,会检测一些文件的权限,是否包含一些安全机制等,并形成一个分析报告。 | Collin Mulliner | Hardware/Embedded,Security Development Lifecycle |
| 95 | Preventing Authentication Bypass: A Tale of Two Researchers | Ravi Jaiswal,Ron Chan,Terry Zhang | Applied Security,Security Development Lifecycle |
| 96 | Securing the System: A Deep Dive into Reversing Android Pre-Installed AppsGoogle Project Zero,Android 系统预装 App 的逆向深度分析 | Maddie Stone | Reverse Engineering,Mobile |
| 97 | Towards Discovering Remote Code Execution Vulnerabilities in Apple FaceTime盘古,Apple FaceTime 的架构、相关攻击面以及一些漏洞 | Tielei Wang,Tao Huang | Exploit Development |
| 98 | Finding a Needle in an Encrypted Haystack: Leveraging Cryptographic Abilities to Detect the Most Prevalent Attacks on Active Directory | Yaron Zinar,Marina Simakov | Network Defense,Enterprise |
| 99 | A Compendium of Container Escapes一篇针对容器逃逸的概述,主要内容包括了 linux 内核容器基础,执行逃逸,docker、RunC等容器的漏洞以及内核漏洞利用的研究 | Nick Freeman,Brandon Edwards | Exploit Development,Platform Security |
| 100 | Adventures in the Underland: The CQForensic Toolkit as a Unique Weapon Against Hackers | Paula Januszkiewicz | Data Forensics/Incident Response |
| 101 | Attacking iPhone XS Max这个议题介绍了 UNIX socket bind 操作因临时 unlock 引发的竞争条件,最终导致了一个 UAF 漏洞,作者介绍了该漏洞在 A12 之前和之后的漏洞利用方法 | Hao Xu,Tielei Wang | Exploit Development,Mobile |
| 102 | Infiltrating Corporate Intranet Like NSA - Pre-auth RCE on Leading SSL VPNs | Meh Chang,Orange Tsai | Web AppSec,Enterprise |
| 103 | Everybody be Cool, This is a Robbery! | Jean-Baptiste Bédrune,Gabriel Campana | Hardware/Embedded |
| 104 | Hacking Ten Million Useful Idiots: Online Propaganda as a Socio-Technical Security Project | Pablo Breuer,David Perlman | Policy,Human Factors |
| 105 | Integration of Cyber Insurance Into A Risk Management Program | Jake Kouns | Cyber Insurance |
| 106 | HostSplit: Exploitable Antipatterns in Unicode Normalization | Jonathan Birch | Applied Security,Web AppSec |
| 107 | Lessons From Two Years of Crypto Audits | Jean-Philippe Aumasson | Security Development Lifecycle,Cryptography |
| 108 | Securing Apps in the Open-By-Default Cloud | Michael Wozniak,Winston Howes | Enterprise,Security Development Lifecycle |
| 109 | Look, No Hands! — The Remote, Interaction-less Attack Surface of the iPhone | Natalie Silvanovich | Mobile,Exploit Development |
| 110 | The Discovery of a Government Malware and an Unexpected Spy Scandal | Lorenzo Franceschi-Bicchierai | Mobile,Malware |
| 111 | MITRE ATT&CK: The Play at Home Edition | Ryan Kovar,Katie Nickels | Data Forensics/Incident Response,Applied Security |
| 112 | The Future of ATO | Philip Martin | Web AppSec,Applied Security |
| 113 | Breaking Samsung’s ARM TrustZone | Joffrey Guilbon,Alexandre Adamski,Maxime Peterlin | Hardware/Embedded,Mobile |
| 114 | Responding to a Cyber Attack with Missiles | Mikko Hypponen | Policy |
| 115 | Worm Charming: Harvesting Malware Lures for Fun and Profit | Pedram Amini | Applied Security,Malware |
| 116 | Command Injection in F5 iRules | Christoffer Jerkeby | Web AppSec,Network Defense |
| 117 | Debug for Bug: Crack and Hack Apple Core by Itself - Fun and Profit to Debug and Fuzz Apple Kernel by lldb Script使用苹果自带的 LLDB Script fuzz macOS 系统内核 | Moony Li,Lilang Wu | Platform Security |
| 118 | Arm IDA and Cross Check: Reversing the Boeing 787’s Core Network | Ruben Santamarta | Hardware/Embedded,Reverse Engineering |
| 119 | Exploring the New World : Remote Exploitation of SQLite and Curl | HuiYu Wu,YuXiang Li,Wenxiang Qian | Internet of Things,Exploit Development |
| 120 | Controlled Chaos: The Inevitable Marriage of DevOps & Security | Nicole Forsgren,Kelly Shortridge | Applied Security,Security Development Lifecycle |
| 121 | How to Detect that Your Domains are Being Abused for Phishing by Using DNS | Karl Lovink,Arnold Hölzel | Policy,Applied Security |
| 122 | Every Security Team is a Software Team Now | Dino Dai Zovi | Keynote |
| 123 | A Decade After Bleichenbacher ‘06, RSA Signature Forgery Still Works | Sze Yiu Chau | Web AppSec,Cryptography |